¶ Standards Overview
Acknowledgements:
Many references contained herein remain the exclusive rights of the original owners of the works.
Inclusion here is for completeness and reference purposes.
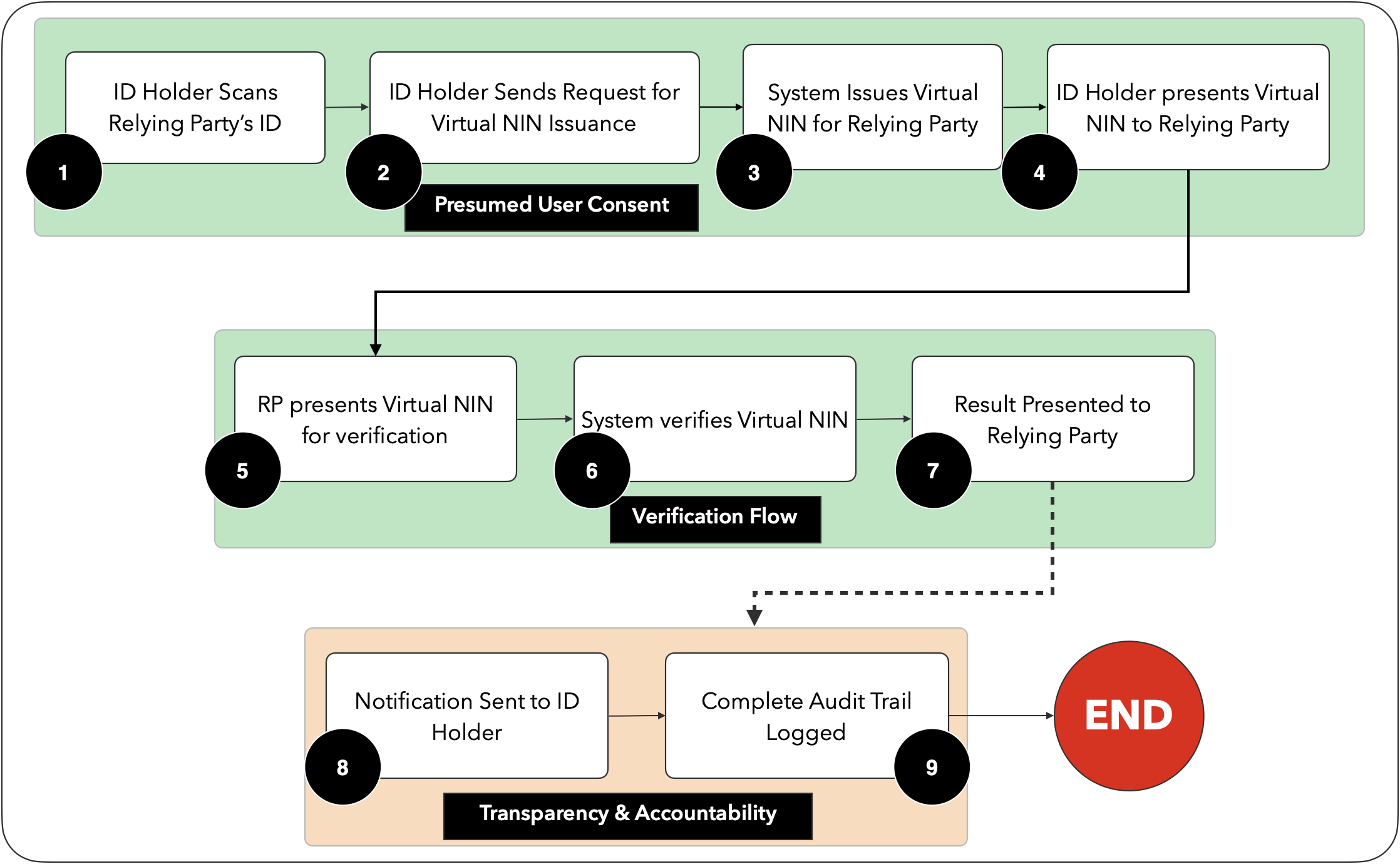
¶ ISO/IEC 7064:2003
To reduce the chances of data entry errors (or counterfeiting), just as Credit Cards employ the use of the Luhn Algorithm for the checksum, the Virtual NIN being rolled out uses the ISO/IEC 7064:2003 MOD 1271-36 MOD661-26 to generate a 2-digit checksum.
¶ Encryption Methodology

Where possible, NIST Elliptic Curve Cryptography is used. They are smaller in size and relatively harder to crack or decode.
In order to deliver payload content, the Digital Identity Tokens have different barcode symbologies used for rapid delivery and scanning.
¶ Aztec Barcodes (ISO/IEC 24778:2008)
Deployment:
- Standard Improved NIN Slip
- Premium Improved NIN Slip
¶ QR Codes (ISO/IEC 18004:2015)
Deployment:
- MobileID ID Card Page
- Virtual NIN ID Page
- Enterprise ID Long Code Delivery
- Onboarding URL

¶ Visible Digital Seals for Non-Electronic Documents
The following concepts were considered and parts adopted in the development and issuance of the Barcode contained on the Improved NIN Slip:
- Asymmetry. Due to using asymmetric cryptography, the cost of attacking a digital seal is considerably higher than the cost of issuing a visa document protected with a digital seal. Thus even though the cost of issuing a document is very low, it is extremely costly to fake or forge it.
- Personalization. Each digital seal verifies the information printed on the physical document, and is thus tied to the document holder. There is no direct equivalent of a blank document, and thus no blanks can be lost or stolen.
- Easy verification. Even an untrained personnel is able to verify a document protected with a digital seal by using low cost equipment, such as an application on a smartphone. Moreover, due to the binary nature of a digital signature, distinguishing between authentic documents and forged ones is easy.
Source: Visible Digital Seal for Non-Electronic Documents, V 1.7, March 2018
<https://www.icao.int/Security/FAL/TRIP/Documents/TR - Visible Digital Seals for Non-Electronic Documents V1.7.pdf. Accessed 12.09.2021 23:09 WAT>
Author: ISO/JTC1/SC17/WG3/TF5 for ICAO-NTWG
¶ Public Key Infrastructure (PKI)
Elliptic Curve Cryptography (ECC) is employed where practicable.
The NIMC and NITDA are collaborating closely to ensure the National Public Key Infrastructure is properly utilised in the issuance and administration of Digital Credentials.
¶ NTP Timestamping
To ensure reliablity of the timestamp presented in verification transactions, the MWS Infrastructure uses the Network Time Protocol (NTP) to synchronise clocks on all systems.
¶ Blockchain Technology
The NIMC MWS Infrastructure uses Distributed Ledger Technology (DLT) to store verification transactions as a failover database. It uses the immutability features to ensure that the information written cannot be altered.
Despite being a permissioned (private) Blockchain, no personally identifiable information (PII) is written to the DLT. Only information relating to the transaction itself (the transactionID, timestamp, UserID of the verifier and the type of verification made) is recorded.
The MWS Infrastructure does not rely on DApps or Smart Contracts in any shape or form.
¶ Open Standards vs Open Source
Though often used interchangeably, Open Source and Open Standards are not the same thing.
Open Source refers to software and other technologies that fall under a General License permitting modification, reuse and restricting ownership of any part of the original code.
Open Standards conversely, refers to one or more Best Practices or Standards that may be adopted for use without any proprietary content contained therein.
In general, Open Source may be treated as a ‘Vendor’ just as one would any other such as Microsoft, Apple or Oracle.
¶ OSIA API Interfaces

In order to reduce the chances of proprietary interfaces creeping into the National Identity Management Infrastructure (NIMS), the NIMC is adopting Open Standards interfaces where possible, and over time.
All interfaces are migrating to RESTful APIs.
¶ General Data Protection Regulations
The Federal Government of Nigeria is rapidly working on a National General Data Protection Regulation (nGDPR), which is loosely modelled around the European GDPR.
Data Privacy is at the forefront of the new Government Initiatives.
¶ Proposed External Audit Reviews
TBD
¶ References
ISO/IEC Aztec Barcode Symbology: https://www.iso.org/standard/41548.html
ISO/IEC 18004:2015 QR Code Symbology: https://www.iso.org/standard/62021.html
ISO/IEC 7064/2003 Security techniques — Check character systems:
https://www.iso.org/standard/31531.html
NIST Elliptic Curve Cryptography: https://csrc.nist.gov/Projects/Elliptic-Curve-Cryptography/
GDPR: https://www.gdpreu.org/
Secure Identity Alliance: https://secureidentityalliance.org/osia/
All references, names and/or brand marks are duly acknowledged.