
The informatiion on this page will be reviewed periodically and updated to provide accurate technical and legal opinions in the interest of transparency and strict adherence to the laws of the Federal Republic of Nigeria.
¶ Overview
There has been discussion in recent times, since the Federal Government of Nigeria approved a new process of establishing enhanced data protection via Tokenization and pseudonomising sensitive information across the country.
In the eyes of the Government (and following International Best Practices in the area of Data Protection), User Consent goes beyond simply asking “can I verify your NIN?” and the ID Holder responding “yes you can”.
Data is often described as the “new Oil”. Under the leadership and supervision of the Ministry of Communications & Digital Economy, the Government is taking very bold steps to ensure that Nigerians enjoy the same levels of security and privacy of personal information as is found in advanced economies around the world.
Nigeria is watched and followed by most African countries, and steps that are taken in Africa’s largest economies are usually the template for others. In this regard, Data Privacy and Protection will be and will remain a critical barometer for the establishment of Digital Economy in the country.
¶ Preamble
- It is to be understood that the Personally Identifiable Information (PII) of the holder of the NIN belongs to that person and not the Relying Party, nor the NIMC or any other Government agency
- The NIMC serves as Custodian of personal identity as well as Regulator of Identity Management as provided for in the NIMC Act of 2007.
- Requesting information on an individual is just that - a request. There is no mandatory right for the NIMC to provide such information outside specific and qualified User Consent or for National Security purposes.
¶ Actors
| Actor | Description |
|---|---|
| ID Holder | A person issued a National Identification Number (NIN). This includes even day-old infants |
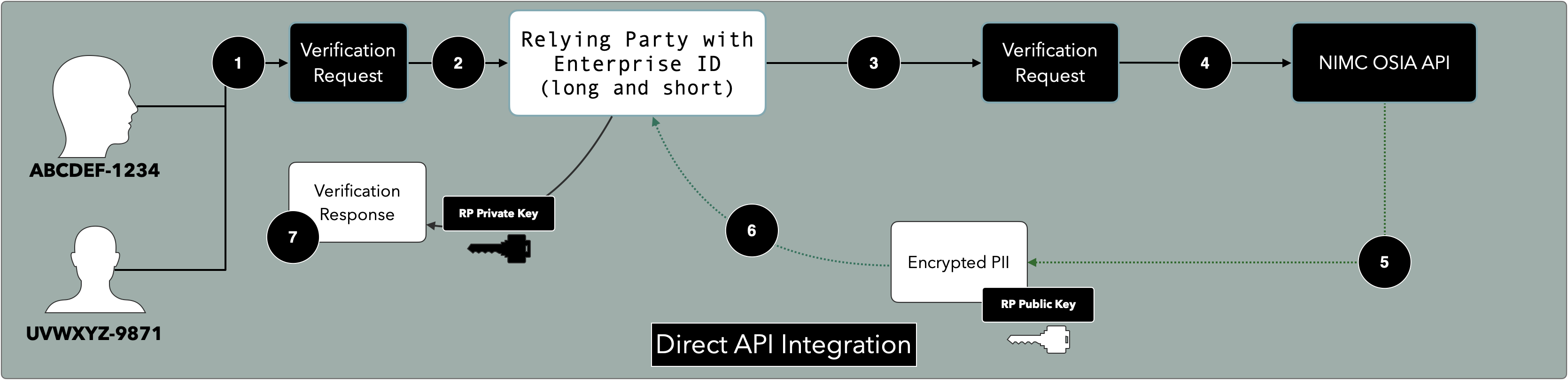
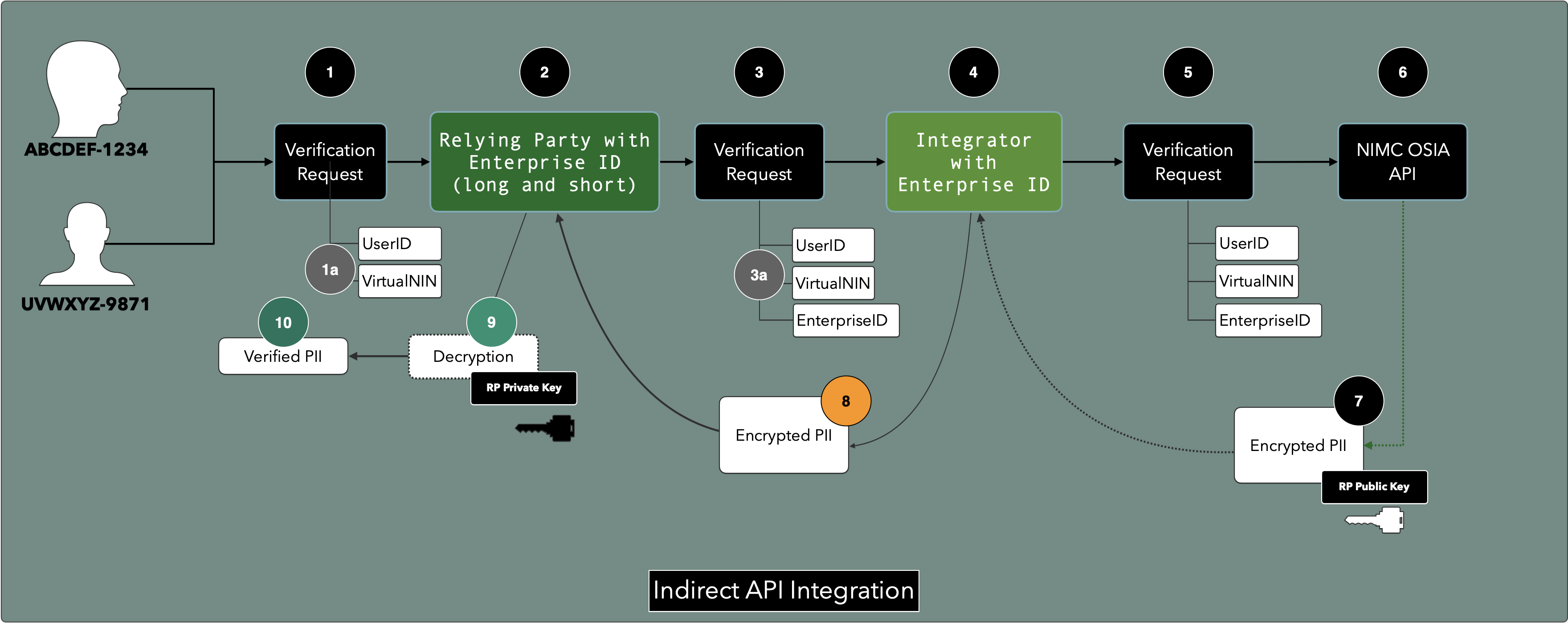
| Relying Party | An entity (natural person or enterprise, including Consular Services of Embassies/High Commissions) who are requesting for information about an ID Holder |
| Agent | An employee or representative of a Relying Party duly authorised (via approved processes by the NIMC) to carry out a request for information of an ID Holder on behalf of the Relying Party (RP) |
| Integrator | An enterprise who acts on behalf of a Relying Party by providing Proxy services (such as API calls to the NIMC) |
| NIMC | Custodian of Personal Identity and singular Regulator of Identity Management in Nigeria |
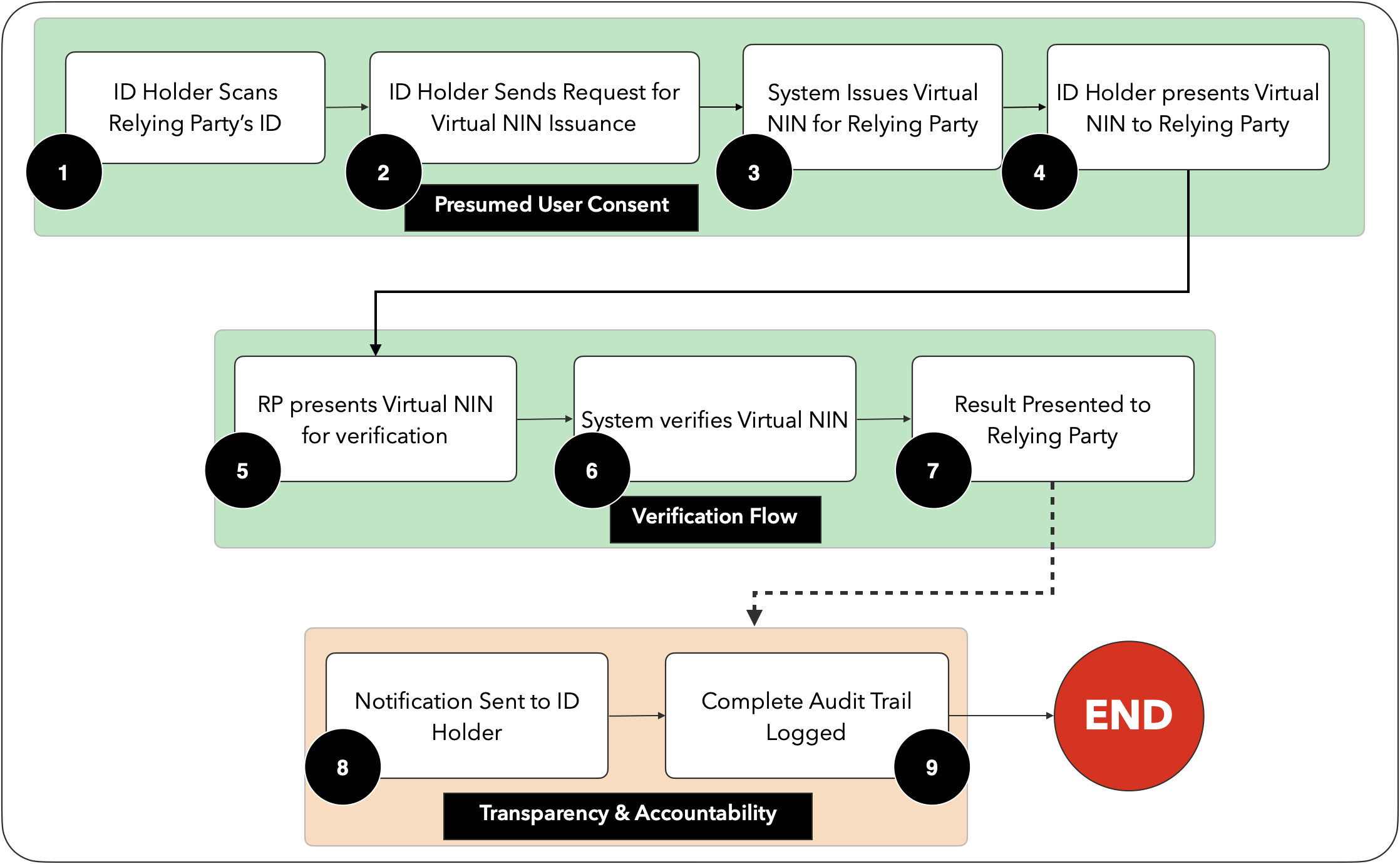
¶ What constitutes User Consent?
-
Full disclosure of what information needs to be processed by the Relying Party. this includes:
(a) Who is requesting the information
(b) Who is actually carrying out the request for information
© How the information is being transmitted
(d) How the information will be stored -
The request must be one time only
-
The one time request is not to be seen as a license to perpetually carry out the same request riding on the first
-
The request must contain information in plain language without technical or legalese language which may confuse the ID holder
-
The User Consent may be withdrawn by the ID Holder
-
The Custodian shall respond to any request by the ID Holder for details of who may have requested for their Personal Information, except where the request was from a National Security endpoint.
-
Where the information is being requested via a Proxy (say an Integrator or Service Provider), the Proxy shall not gain access to the information simply because it served as a conduit, nor shall it attempt to decrypt the information in transit.
¶ References
- GDPR User Consent: https://gdpr.eu/gdpr-consent-requirements/
- Lukas Zolejnik How to: GDPR, consent and data processing
- IAPP ► The UX Guide to getting consent
- Tilburg University ► Consent now and then
- Oxford University Press ► Commentary on the EU General Data Protection Regulation (GDPR) – Lawfulness of processing, Page 32